We’re excited to bring an updated repository list view experience and the ruleset merge queue rule to general availability, as well as an update to the status check and workflow rules.
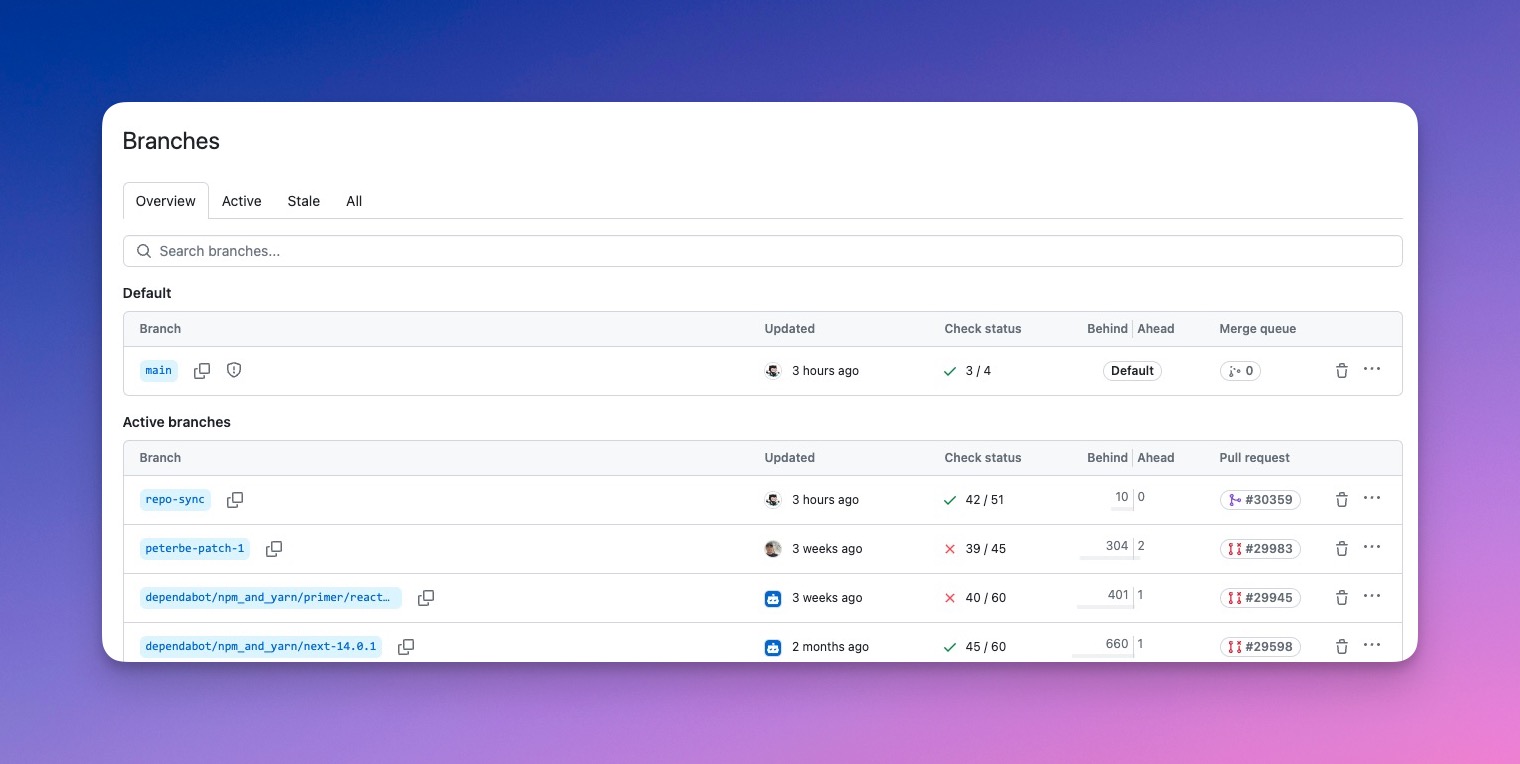
Finding repositories in your organization is now easier
With the introduction of custom properties earlier this year we wanted to make it easier to find repositories across your organization. With the new organization repository view and advanced filtering you find repositories based on common parameters like visibility and language, but also custom properties, size, license and a host of additional values.
Repository Rules updates
Repository ruleset merge queue rule is now generally available
In addition to being able to manage your merge queue via rules, you can now see all the pull requests that merged in the same group along with the checks needed for the queue with rule insights.
Learn more about merge queues in our documentation and repository rules REST API
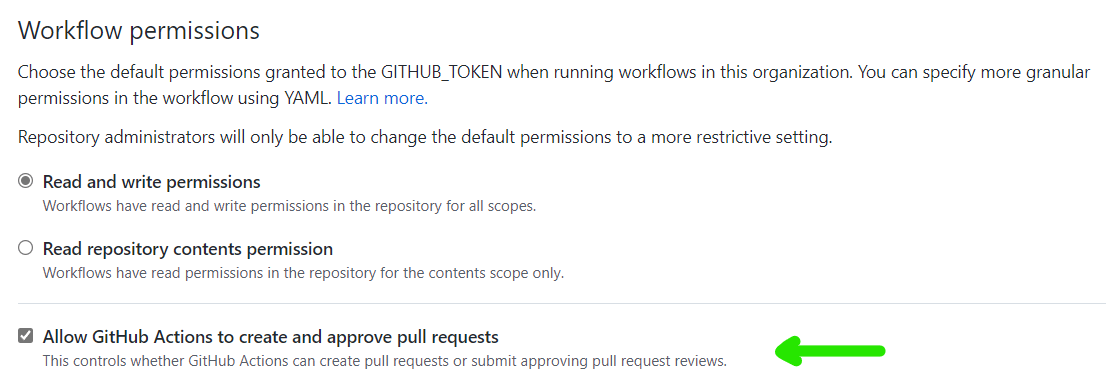
Avoid required status checks and required workflows when creating branches
Applying status check and actions workflow rules to newly created branches has been a point of friction in rulesets. When creating a new branch will fail unless you add bypass actors or create an intermediate unprotected branch. To alleviate this friction there is a new option available prevent checks and workflows from running on new branches.
Learn more about status check rules and required workflows rules in our documentation.
Join the discussion within GitHub Community.